
WHY DO I NEED ACCESS MANAGEMENT?
Access Management adds value to a defense-in-depth approach to cybersecurity. Access Management is about ensuring that end users have the right access to the right applications at the right time. Not only will you be able to balance security with productivity, but you will be able to report on access to your systems (compliance).
HOW CAN OUR ACCESS MANAGEMENT SOLUTIONS HELP YOU?
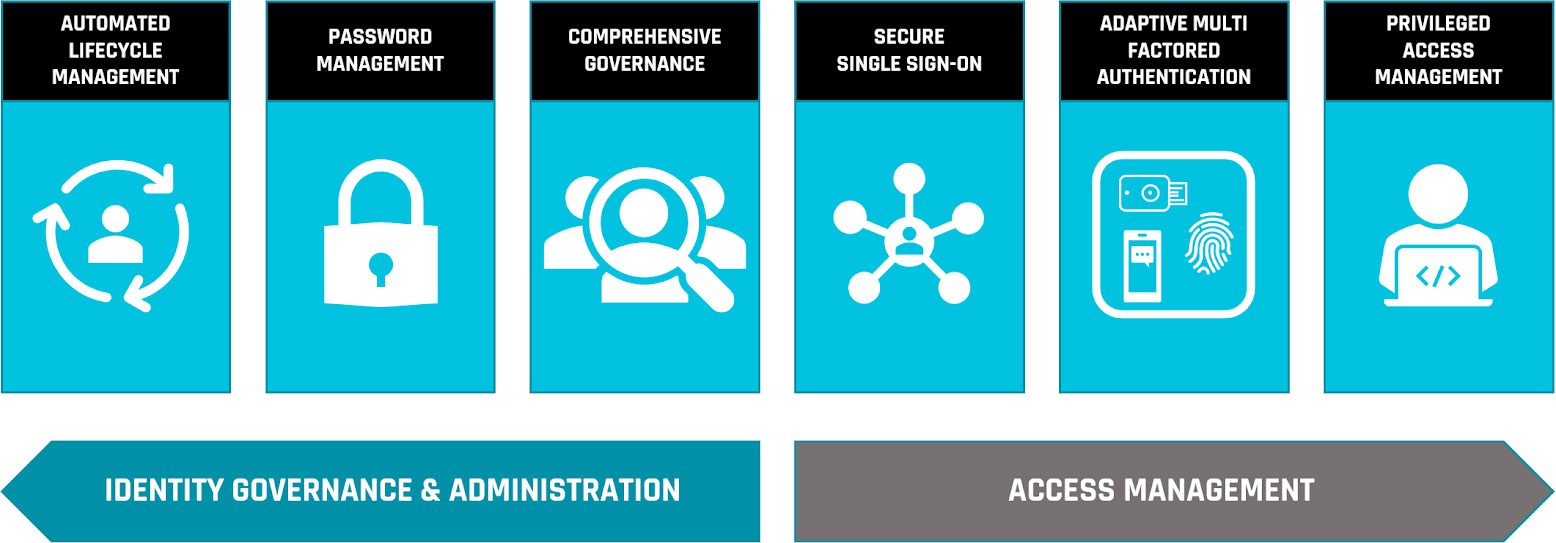
Our access management solutions provide you with the following:
- Provisioning
- Secure Single Sign-On
- Adaptive Multi-Factor Authentication
- Privileged Access Management
Our Access Management Solutions Covers These Key Areas:
 PROVISIONING
PROVISIONING
Access Management adds value to a defense-in-depth approach to cybersecurity. Access Management is about ensuring that end users have the right access to the right applications at the right time. Not only will you be able to balance security with productivity, but you will be able to report on access to your systems (compliance)
SECURE SINGLE SIGN-ON
Single Sign-On is the process of using one authentication (Login) to access different applications that can be internal to an organization or external (SaaS). This is not to be confused with password synchronization (which can be accomplished with most Identity Management provisioning systems). Single Sign-On can reduce helpdesk calls, make your employees more productive and can enable federation with other vendors or customers.
Our Single Sign-On solutions include products from Identity Automation, Micro Focus, OneLogin, and Microsoft. We provide solutions that will fit all organizations.
ADAPTIVE MULTI-FACTOR AUTHENTICATION (MFA)
Most online access management systems are now utilizing some form of Multi-Factor Authentication (MFA) to access our accounts on the internet. Having a password and a 2 Factor/MFA login process will make your organization secure from leaked password lists and most phishing attacks.
We also recommend using adaptive MFA when possible. Adaptive uses either AI or a risk score (based upon location, systems, targeted systems, etc) to validate if further confirmation is required to authenticate your users.
Testimonials
![]()
We've been very pleased with the Concensus team ever since we made the decision to switch from handling our own IT to their managed services. Maybe the biggest benefit is just feeling so much more confident in our security.

![]()
Concensus Technologies helped my firm tremendously. We had an email related issue recently. The Consensus team was able to log into our system pinpoint and resolve the issue quickly. No fuss, just effective. We will continue to rely on them as we grow.

![]()
My team at American University is an enthusiastic customer of the "Primary Engineer" program thru Concensus. Having a predictable monthly spend for world class talent has allowed my team to respond more than 3 times faster to stakeholder requests. Concensus has made our Identity Program better.

Let us give you peace of mind
Leave it to our experts to keep your organization secure around the clock. Partner with us for trusted technology support.
