
Managing the digital identity lifecycle is what we do at Concensus Technologies.
With partnerships with top-tier vendors such as Identity Automation, Micro Focus, One Login, Okta & Beyond Trust we can complete the life cycle management of your digital identities.
We have experience with implementing identity management solutions that will fit the most common tasks to highly complex solutions for large enterprises.
Some of the key benefits of Identity Management Solutions:
- Automated onboarding and offboarding of user identities
- Automated license management for cloud-based applications
- A first step to automating your zero-trust initiative
- Meeting your compliance requirements
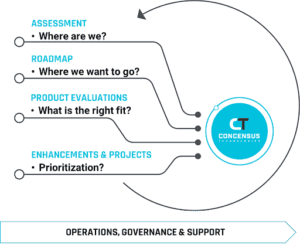
Ensuring success – Our Identity Management Process
An identity management solution needs to be tailored to your organization. There are no cookie-cutter implementations of ID management that will allow you to meet your goals.
THE IDENTITY MANAGEMENT ASSESSMENT
Organizations that approach their Identity Management program with a tactical approach often fail. An assessment will help your organization plan or modernize your existing Identity Management solution. While a large enterprise may need a strategy engagement that encompasses many departments and need to build a use case, smaller organizations may only need to build use cases and ensure that they are considering all implications of an identity management solution.
The Identity Management Roadmap
The roadmap allows us to discover opportunities for implementing an identity management solution. The roadmap looks 18-36 months into the future to help build a comprehensive phased approach to not just Identity Management but to Single Sign-On, Access Management, Reporting, Governance, Multi-Factored Authentication, Privileged Access Management and Password Management.
Identity Management Product Evaluations
Product evaluations are necessary to match the correct technology with people and your processes. Finding the right fit will help maximize your investment, your security and efficiency.
IDENTITY MANAGEMENT ENHANCEMENTS AND PROJECTS
At Concensus we have done over 200 projects that include:
- New Implementations
- Major Upgrades
- Migrations from one platform to another
- Replacing authoritative sources (Student Information Systems, HR Systems)
- Custom Development of Application Connectors
- Business to consumer identity (over 2 million subscribers)
Our projects follow a successful methodology that is customized to meet customer needs and budget. We offer Identity Management projects (Time & Materials/Fixed Fee) and through our Managed Services offerings. Let us Manage your IaM environment for you!
FAQs for Identity Management Solutions
Testimonials
![]()
We've been very pleased with the Concensus team ever since we made the decision to switch from handling our own IT to their managed services. Maybe the biggest benefit is just feeling so much more confident in our security.

![]()
Concensus Technologies helped my firm tremendously. We had an email related issue recently. The Consensus team was able to log into our system pinpoint and resolve the issue quickly. No fuss, just effective. We will continue to rely on them as we grow.

![]()
My team at American University is an enthusiastic customer of the "Primary Engineer" program thru Concensus. Having a predictable monthly spend for world class talent has allowed my team to respond more than 3 times faster to stakeholder requests. Concensus has made our Identity Program better.

Let us give you peace of mind
Leave it to our experts to keep your organization secure around the clock. Partner with us for trusted technology support.

